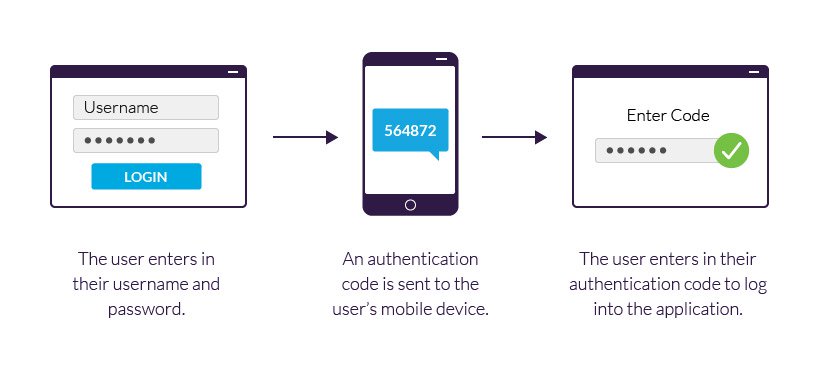
1) Big idea with an everyday example
Two-Factor Authentication (2FA) makes you prove “it is really you” in two different ways—usually a password (something you know) plus a code/device/biometric (something you have or are).
Think of an ATM: you need the card (have) + PIN (know). If a thief has only one, money stays safe. Online 2FA is the same: even if your password leaks, the attacker is stopped at the second step.
2) What actually happens during login and which second factor to pick
You enter username + password. The site then asks for a second factor. Common options:
-
Authenticator app code (TOTP): A 6-digit code that changes every ~30 seconds and works without mobile data or SMS.
-
Security key (USB/NFC; FIDO2/WebAuthn): A small hardware key you tap; highly phishing-resistant.
-
Push notification: A prompt on your phone—tap Approve to log in.
-
SMS OTP (One-Time Password by text): A code sent by SMS.
-
Biometric: Fingerprint or Face ID (usually inside your device’s passkey flow).
Which should you choose?
-
Best: Authenticator app or Security key (strong and reliable).
-
Good: Push notification (easy—just do not approve blindly).
-
Okay: SMS OTP (better than nothing, but weaker against SIM-swap and telecom tricks).
3) Set it up in 2 minutes
Turn on Two-Factor Authentication in Settings → Security. Prefer an Authenticator app or a Security key.
Quick setup checklist
-
Enable Two-Factor Authentication
-
Pick Authenticator app and scan the QR
-
Save backup codes safely (paper or password manager)
-
Add a backup second factor (second device or security key)
-
Turn on login alerts
Story: Ravi’s email password leaks from another site. A hacker tries to log in, but the account asks for Ravi’s app code. The hacker does not have it → blocked. Ravi changes his password. 2FA saved the account.
4) If you lose your phone — how to recover
Do not panic.
-
Use your backup codes or security key to sign in.
-
Then move 2FA to your new phone (re-scan the QR in settings).
-
If fully locked out, contact support and be ready with ID proof.
-
For the future, keep two second factors (for example, app + key).
5) Simple safety tips and common mistakes to avoid
-
Use a strong, unique password + 2FA for email, banking, cloud, and social media.
-
Never share OTP or codes with anyone—even if they claim to be “support”.
-
Beware push fatigue: Do not approve a push prompt you did not start.
-
Prefer Authenticator app/Security key over only SMS OTP.
-
Review active devices/sessions monthly; sign out of what you do not recognise.
6) Tiny glossary (quick meanings)
-
TOTP (Time-based One-Time Password): Code from an authenticator app; works offline.
-
Security key: A hardware key using public-key cryptography; resists phishing.
-
Push prompt: An approval popup on your phone; convenient but risky if you click without checking.
-
SIM-swap: Fraud where your mobile number is hijacked; this is why SMS-only 2FA is weaker.
Prelims Practice (MCQ)
Q. With reference to two-factor authentication and similar login technologies, consider the following statements:
-
Time-based codes from an authenticator app can work even without mobile data or SMS.
-
Hardware security keys (FIDO2/WebAuthn) use public-key cryptography and are generally phishing-resistant.
-
SMS OTP is safer than authenticator apps because it cannot be affected by SIM-swap or telecom routing attacks.
-
Push-to-approve notifications can be abused through “MFA fatigue” when users approve prompts they did not start.
Which of the statements given above are correct?
A. 1 and 2 only
B. 1, 3 and 4 only
C. 1, 2 and 4 only
D. 1, 2, 3 and 4
Answer: C (1, 2 and 4 only)
Why: (1) True—codes are generated locally. (2) True—security keys are designed to resist phishing. (3) False—SMS can be hit by SIM-swap. (4) True—push prompts can be spammed; careless approvals allow access.
Bottom line: Passwords can leak. Second factors do not. Turn on 2FA—prefer an authenticator app or a security key—and keep backup codes safe.
Start Yours at Ajmal IAS – with Mentorship StrategyDisciplineClarityResults that Drives Success
Your dream deserves this moment — begin it here.